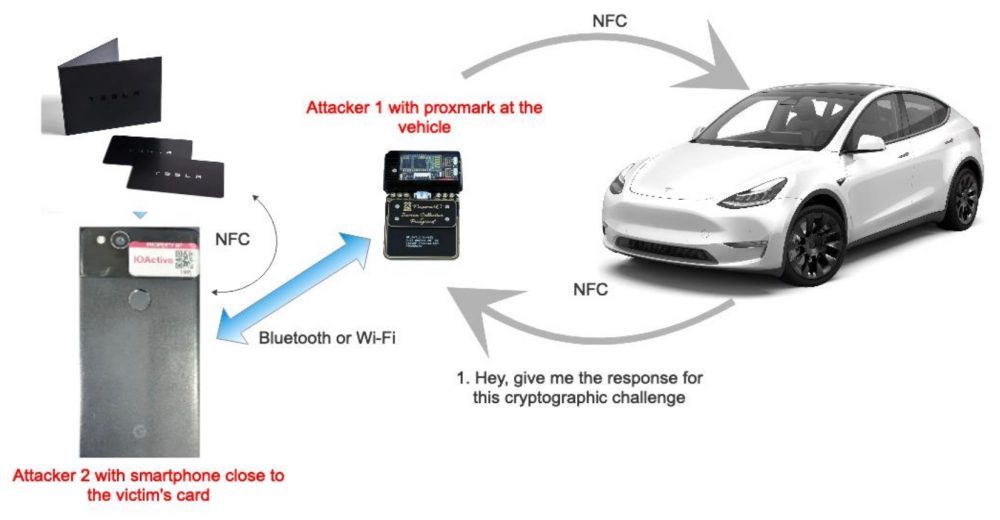
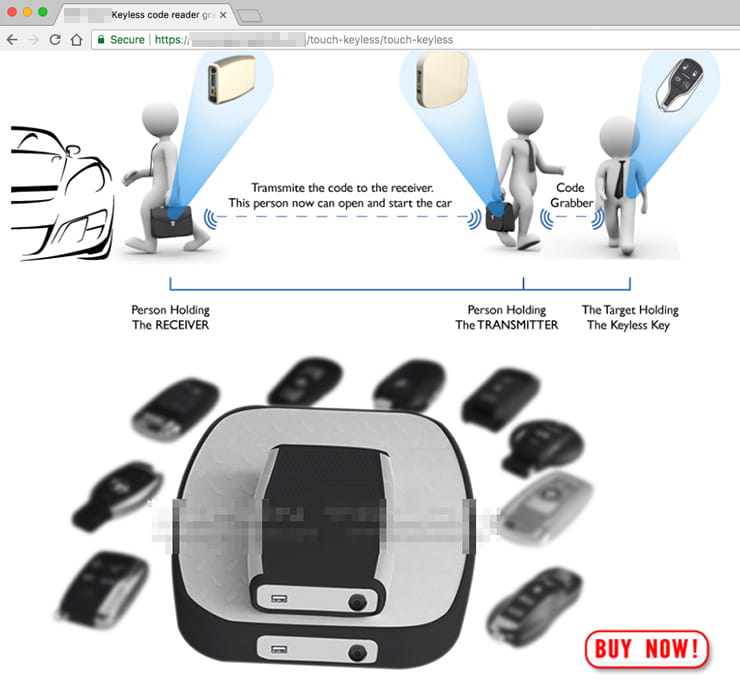
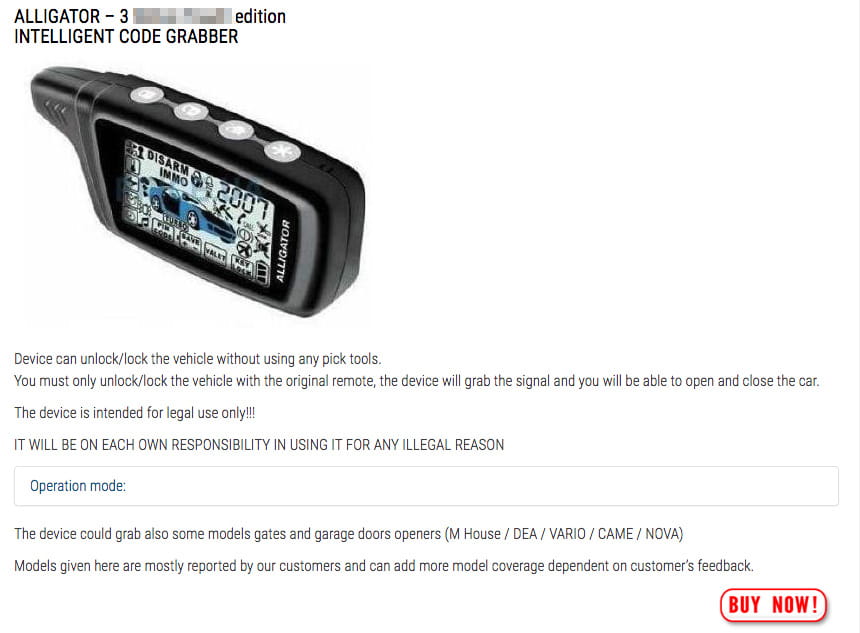
Car-Theft “Mystery Device”: Guarding against a Potential Problem, Real or Imagined – Feature – Car and Driver

How thieves are exploiting £100 eBay gadgets to steal your keyless car in under 30 seconds | The Sun

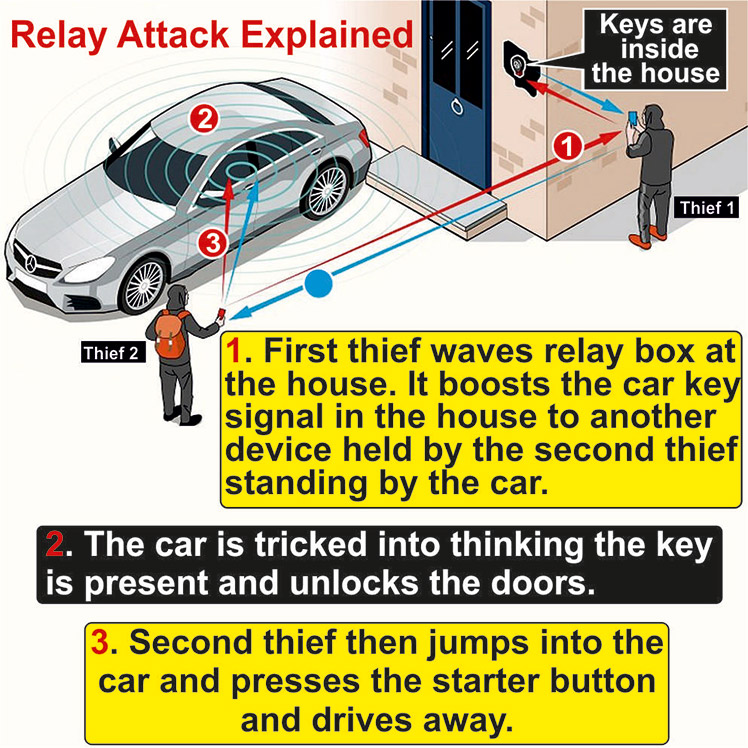
Keyless car theft: What is a relay attack, how can you prevent it, and will your car insurance cover it? | Leasing.com

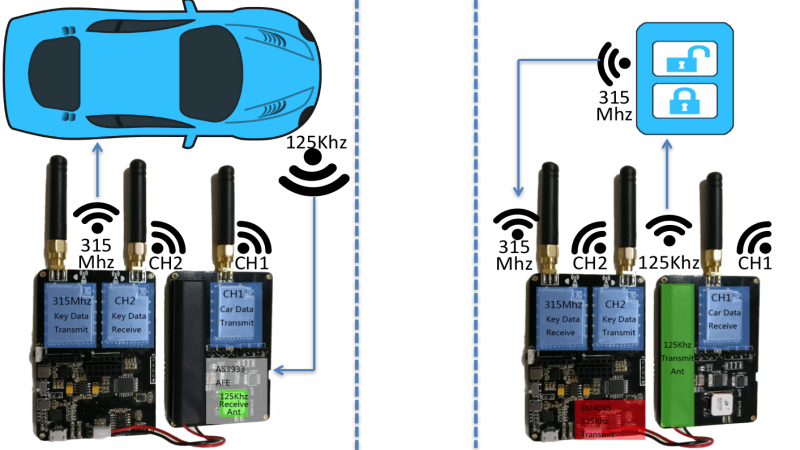
Car Theft with DIY Repeater Amplifier - Relay attack real device! Let's see how we can prevent this - YouTube
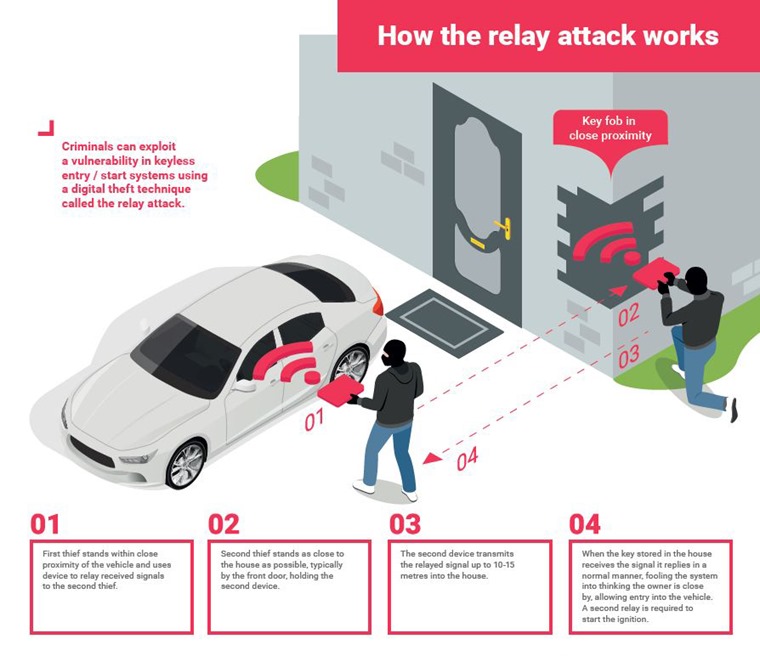
Keyless car theft: What is a relay attack, how can you prevent it, and will your car insurance cover it? | Leasing.com
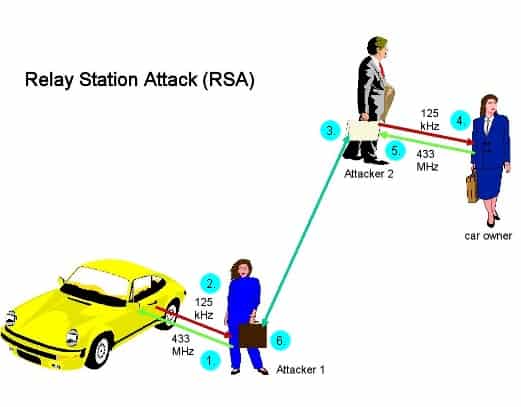
Distance and angle checking: A relay attack on OptiSec3D would need to... | Download Scientific Diagram